802.1x is a Security Protocol at Layer 2 Network Devices
Such as Network Switches and Wireless Access Points
First Step Connect Network Switch to Authenticator Server (RADIUS , Cisco ACS ,…)
When Client want to connect to Network Switch. that switch port changed to unauthorized state
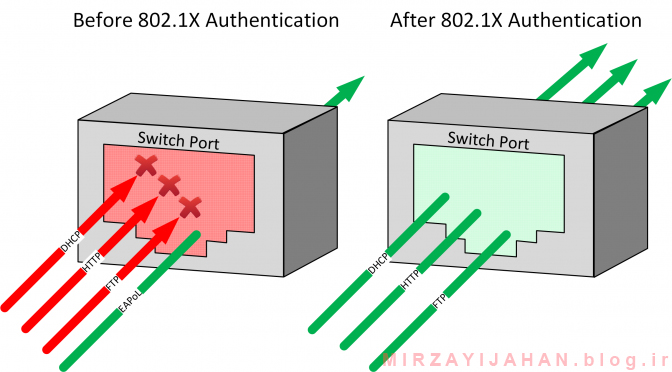
Note: STP & CDP Protocol are enable in this state
That way client must be authenticate via Username and Password to access the network Resources
There are other ways to authenticate
- Mac authentication
- Web authentication
Securing the authentication by EAP mechanism
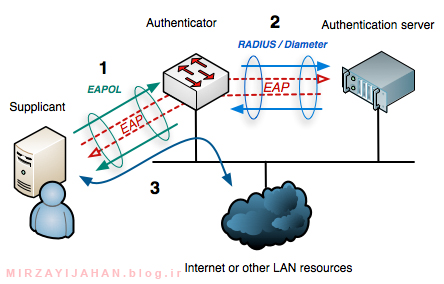
There are several types of EAP
- EAP-PEAP
- EAP-TTLS
- EAP-TLS
- EAP-MD5
- LEAP
- EAPOL
They differ in complexity levels of the security method
Why we must Implement the 802.1X Protocol at the Network?
Many of the network attacks it happens at the Layer 2 Network
And we Don’t have any control over them
But we can using the 802.1X Protocol to Security and authentication users at the network
Why some administrator prefer don’t to use the 802.1x at network?
- Requires to failover Authenticator Server
- Requires to Implementation knowledge
Arman MirzaeiJahan
Best Regards
